In this world of secure digital communication, Public Key Infrastructure (PKI) is an important term. You’ll spot it usually on the SSL certificate issuer websites. In this article, we’ll see what is PKI and the purpose served by it.
What Is Public Key Infrastructure (PKI)?
When you opt to get a digital certificate, you usually generate a CSR in Control Panel and provide it to certificate issuing authority. Generating CSR along with domain information, also generates a pair of key. One of these key is private key. Private key is secret to each entity and it only used for signing. While the other key from pair is public key. The public key is not a secret (as the name also suggests) key and it is used only for verification. That public key uses public key cryptography. PKI is basically used to authenticate users in digital world using public key cryptography. PKI is utilized to associate a key securely with an entity such as user, organization, program, process etc. Different type of hardware, software such as web browsers, email clients have different standard based PKI support which they use to distinguish each other.
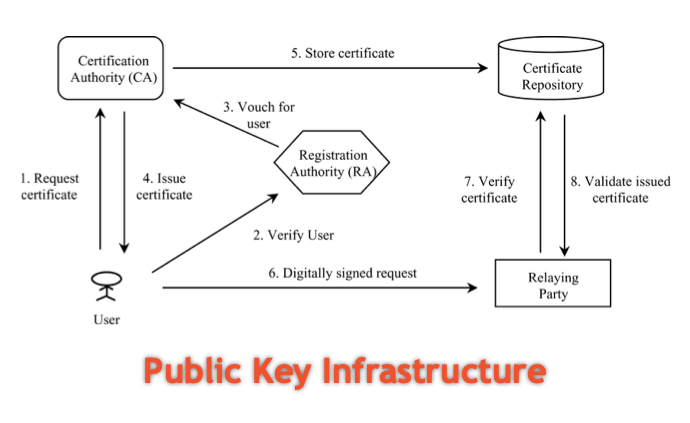
The most common usage of PKI we know is to create, store and distribute digital certificates which is used to verify identity of particular entity. Following are the main components of PKI:
1. Certificate Authority (CA): Entities such as clients may request for digital certificate from CA. It digitally signs, issues and offers the public key to a client requested it.
2. Registration Authority (RA): When the CA is third-party associate from client and system, it is RA. It verifies the issuance of digital certificates by CA.
3. Central directory: It stores to keys and index them securely.
4. Certificate Management System: Manages access to stored certificate and delivery of issued certificates.
5. Certificate policy: Allows the public to check PKI’s honesty.